- Published on
Restrict organization creation with the Microsoft Entra tenant policy in Azure DevOps
- Authors
- Name
- Alexander Arana Escobedo
Prerequisites
- Azure DevOps
- Organization Connection: Ensure your organization is linked to Microsoft Entra ID.
- Azure Subscription and Permissions
- Global Administrator: This is the highest privilege role in Microsoft Entra ID and allows you to manage all aspects of the directory, including assigning roles.
- or Privileged Role Administrator: Can manage assignments for most roles in Microsoft Entra ID, including the Azure DevOps Administrator role.
Intro
When setting up your first organization in Azure DevOps (ADO), it’s easy to overlook the restriction on who can create new organizations. By default, any ADO user can create a new organization, so enabling this policy helps you maintain control over your setup.
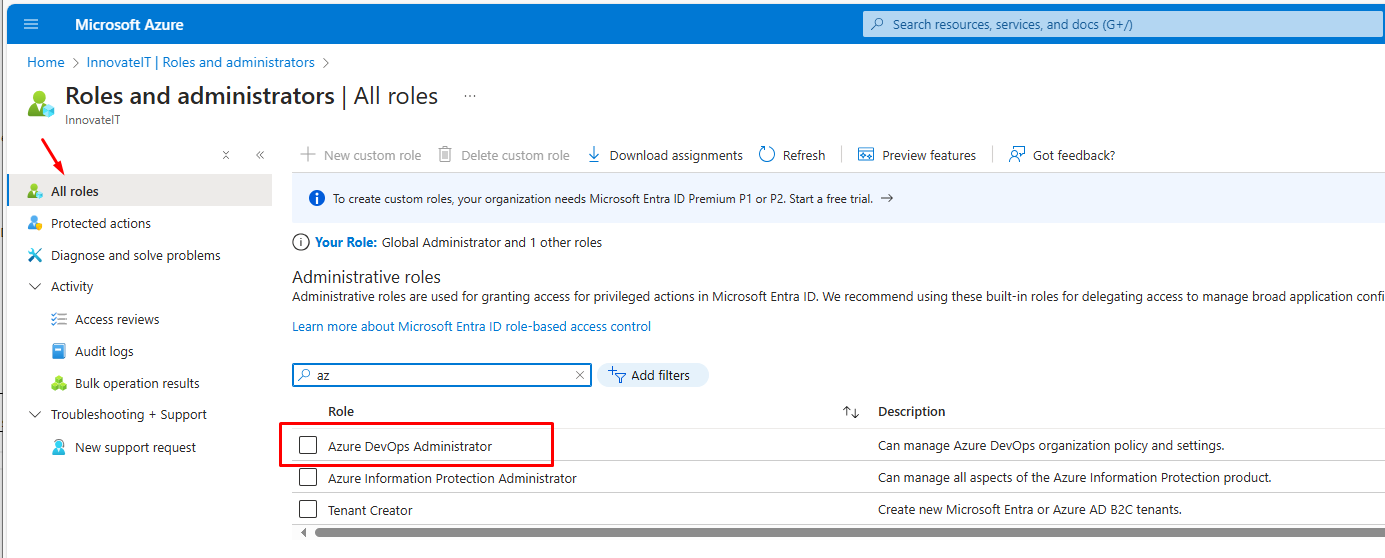
Step 1: Verify Azure DevOps Administrator Role
Ensure you have the Azure DevOps Administrator role in Microsoft Entra ID by navigating to Roles and administrators. If you’re not currently assigned this role, add yourself to it.
Step 2: Access the Azure DevOps Portal
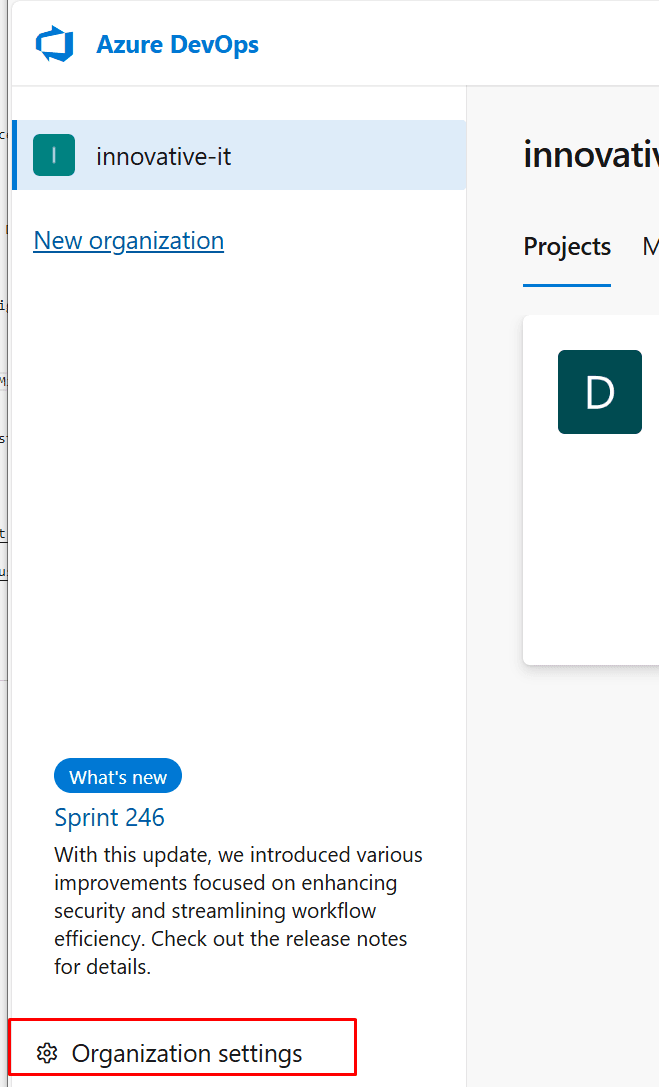
In the Azure DevOps portal, go to Organization settings and navigate to Microsoft Entra.
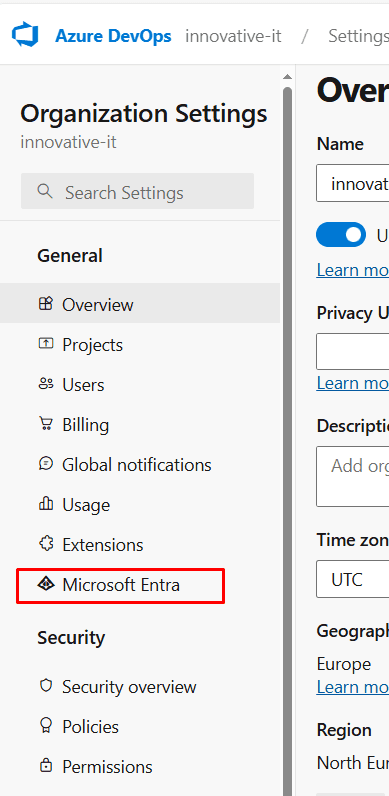
Attn: Sometimes, the Microsoft Entra policy screen might not load correctly. If that happens, copy the URL and open it in a new browser tab.
Enable the Restrict Organization Creation policy:
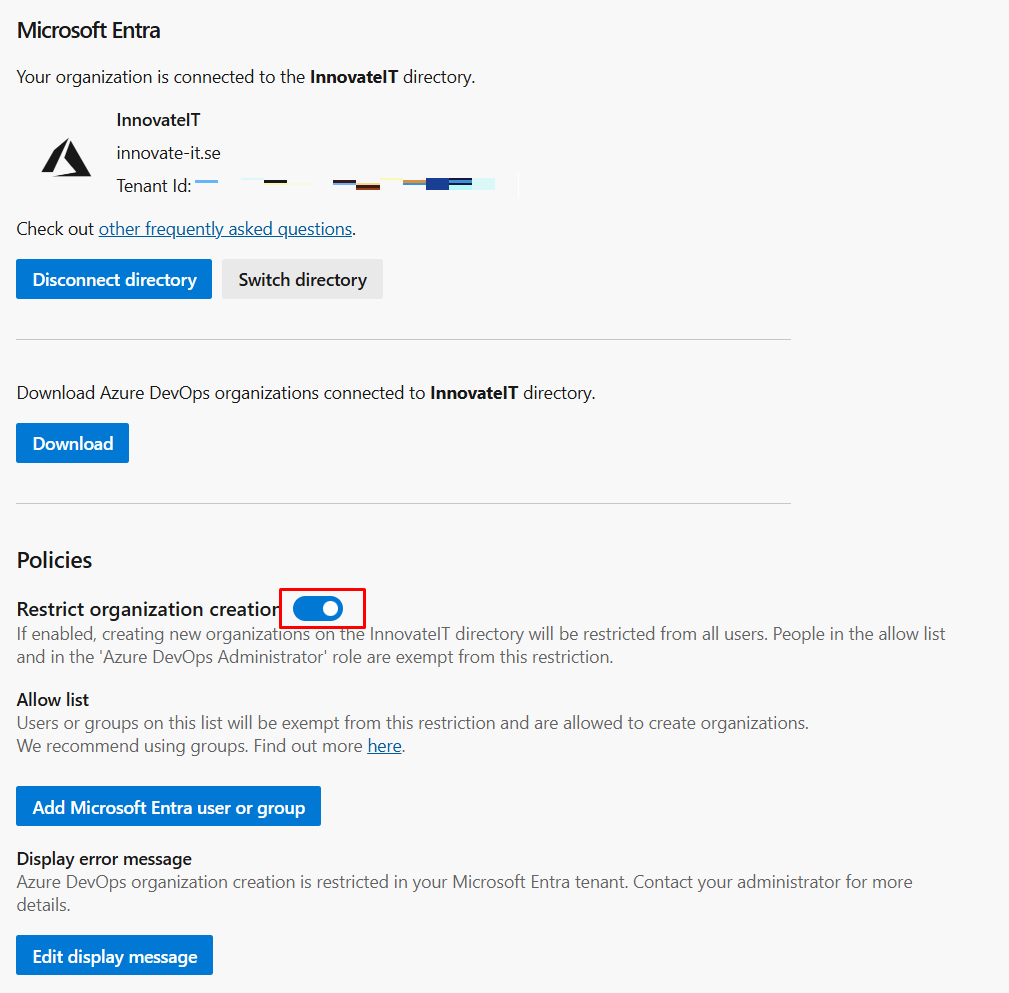
If you scroll further, you'll also find options to enable Restrict Global Personal Access Token and Restrict Full-Scoped Access Token policies, which are highly recommended for added security. For more details on these policies, click here.
That's it! It's a simple yet powerful policy to enhance your organization's security in Azure DevOps.
I hope this guide helps you out! If you have any questions, don't hesitate to reach out.
Alexander Arana.E
References:
Restrict organization creation via Microsoft Entra tenant policy